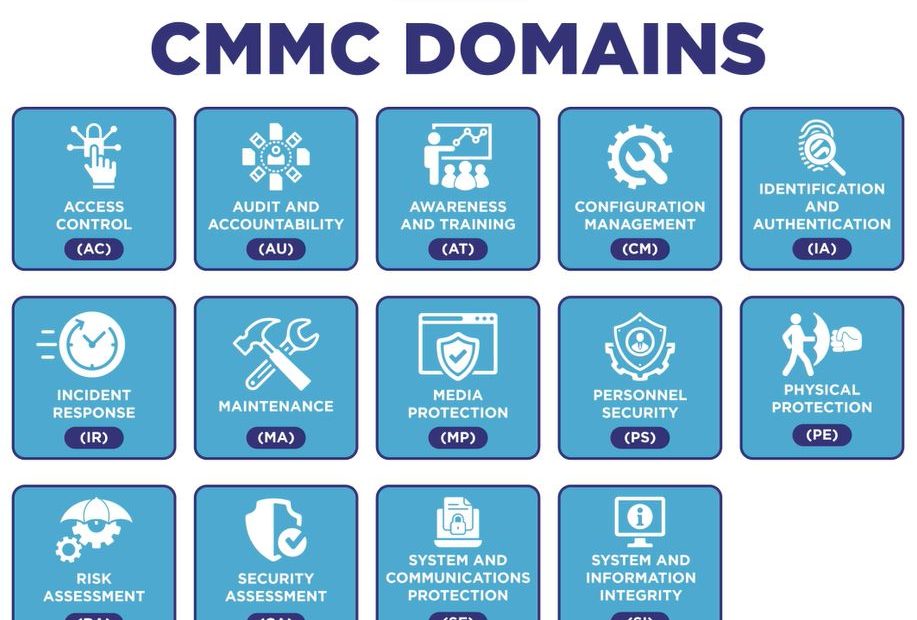
To enhance cybersecurity, CMMC 2.0 blends key federal regulations (48 CFR 52.204-21, DFARS 252.204-7012, NIST SP 800-171, NIST SP 800-172). It streamlines these into 17 domains and 43 capabilities, simplifying the creation of a CMMC cybersecurity plan. The required capabilities hinge on the contractor’s designated CMMC level.
Provided is a breakdown of the 43 CMMC capabilities and their correlation with the 17 domains within the CMMC 2.0 model.
17 Domains
Access Control (AC)
- Establish system access requirements
- Control internal system access
- Control remote system access
Asset Management (AM)
- Identify and document assets
Audit and Accountability (AU)
- Define audit requirements
- Perform auditing
- Identify and protect audit information
- Review and manage audit logs
Awareness and Training (AT)
- Conduct security awareness activities
- Conduct training
Configuration Management (CM)
- Establish configuration baselines
- Perform configuration and change management
Identification and Authentication (IA)
- Grant access to authenticated entities
Incident Response (IR)
- Plan incident response
- Detect and report events
- Perform post-incident reviews
- Test incident response
Find More: Know how the CMMC consulting services help organizations.
Maintenance (MA)
- Manage maintenance
Media Protection (MP)
- Identify and mark media
- Protect and control media
- Sanitize media
- Protect media during transport
Personnel Security (PS)
- Screen personnel
- Protect CUI during personnel actions
Physical Protection (PE)
- Limit physical access
Recovery (RE)
- Manage back-ups
Risk Management (RM)
- Identify and evaluate risk
- Manage risk
Security Assessment (CA)
- Develop and manage a system security plan
- Define and manage controls
- Perform code review
Situational Awareness (SA)
- Implement threat monitoring
System and Communications Protection (SC)
- Define security requirements for systems and communications
- Control communications at system boundaries
System and Information Integrity (SI)
- Identify and manage information system flaws
- Identify malicious content
- Perform network and system monitoring
- Implement advanced email protections
Organizations showcase compliance through various practices and processes. Practices involve technical activities, with 171 mapped across CMMC levels.
Processes gauge an organization’s maturity in implementing cybersecurity procedures. Nine practices are mapped across maturity levels.
The illustration below depicts the distribution of 171 practices across 17 domains. Domains, listed on the left, show practice numbers in each maturity level through color.
Six domains hold 105 out of 171 practices, including:
- Access Control
- Audit and Accountability
- Incident Response
- Risk Management
- System and Communications Protection
- System and Information Integrity
Also Read: How to delete duplicate MP4 files on Mac?
Who needs CMMC certification?
Under DFARS 252.204-7012, DoD contractors used to handle their cybersecurity practices. Monitoring compliance was on them before CMMC.
Contractor audits were rare, and they often self-attested security levels. This led to inconsistent compliance with security requirements.
CMMC 2.0 changes things. All CMMC level 3 (and many CMMC level 2) DoD contractors must undergo independent audits by certified third parties. This ensures a more secure framework. For a better comprehension, please go through the following points:
- Companies collaborating with the U.S. Department of Defense must secure CMMC certification for services or goods provision.
- Various entities in the defense supply chain, including manufacturers and service providers, are obliged to obtain CMMC certification.
- Both prime contractors working directly with the DoD and subcontractors in the defense supply chain must adhere to CMMC requirements.
- Entities managing Controlled Unclassified Information (CUI), like technical and export-controlled data, are under the CMMC certification mandate.
- Any participant in the defense supply chain, irrespective of size or role, might need CMMC certification if dealing with sensitive data.
- Research and Development (R&D) organizations working on defense-related projects may need CMMC certification, especially for classified information.
- Organizations handling Federal Contract Information (FCI), not intended for public release, might require CMMC certification.
- Entities aiming for future DoD contracts involving controlled information must consider obtaining CMMC certification.
- CMMC certification levels vary based on project sensitivity, ranging from Level 1 (basic cyber hygiene) to Level 5 (advanced security practices).
What CMMC level do I need?
As per the OUS A&S statement, the DoD will specify the required CMMC level in solicitations and RFIs. By 2026, DoD-contracted businesses must comply with CMMC, excluding those dealing solely with COTS.
This rule applies to prime contractors, subcontractors, and suppliers throughout the supply chain. Each DoD contract will outline the CMMC level for contractors, creating varied requirements even within a single contract.
For instance, a prime contractor may need CMMC Level 3, while subcontractors meet Level 1. The CMMC-AB collaborates with the DoD to provide independent assessors for contractors at each CMMC level.
You may also like
-
Enhancing Customer Engagement: Innovative Applications of Clarity Voice’s Communication Solutions
-
Solar Energy Solutions: A Sustainable Step Toward Long-Term Growth
-
AI Story Generator Free: A Smarter Way to Spark Creativity
-
Modern Technologies in 2025: AI and Innovative Solutions
-
Mastering Odoo Implementation for Business Success